DevSecOps Tools for Modern Enterprises: Enhancing Security and Productivity
DevSecOps has gone from being a novel idea to a must-have for operations. Software architectures are getting more complicated, and security threats are getting smarter. While DevOps has streamlined the development pipeline, integrating security within that pipeline—DevSecOps—remains a challenge that requires a nuanced approach and a robust toolkit.
In this article, we dissect the critical elements of a DevSecOps toolkit, focusing on the following:
- Intelligent security scanners and their role in automating vulnerability assessments
- Configuration as code for establishing immutable infrastructure
- CI/CD security gates that act as quality control mechanisms for code integrity
- Real-time threat monitoring and forensics for proactive security measures
- Resilience and chaos engineering as methodologies for stress-testing system vulnerabilities
- Compliance automation to ensure adherence to regulatory standards
We also discuss CloudBolt’s upcoming cloud cost management feature, examining how cost considerations can be seamlessly integrated into a DevSecOps strategy. By the end of this article, you’ll have a comprehensive understanding of the critical tools and practices for implementing a DevSecOps pipeline that is secure, cost-effective, and compliant.
Summary of key DevSecOps tools concepts
The following table succinctly encapsulates the core DevSecOps concepts explored in depth throughout this article, providing a quick reference guide for DevSecOps professionals.
| Key element | Description |
|---|---|
| Intelligent security scanners | Beyond basic vulnerability scanning, modern tools use AI and machine learning for predictive security. |
| Paved roads in DevSecOps | Tools that streamline secure development workflows, offering self-service options to maintain the security standards of a DevSecOps model. |
| CI/CD security gates | Leveraging tools that help implement security checks as quality gates in CI/CD pipelines for real-time risk assessment. |
| Threat monitoring and forensics | Tools that offer not just real-time monitoring but also forensic capabilities for post-incident analysis. |
| Resilience and chaos engineering | Tools that help with testing the resilience of your systems against security threats. |
| Compliance automation | Tools that automate compliance checks and generate real-time reports for audits. |
| Cloud cost management | Cloud cost management tools enable DevSecOps teams to monitor, analyze, and optimize cloud expenditures in real time, ensuring that security measures are cost-effective. |
The importance of key elements in DevSecOps
As we delve into the specifics of DevSecOps tools, it’s crucial to understand the significance of certain key elements that form the backbone of this approach. DevSecOps is not just about integrating security practices into development and operations—it’s about leveraging specific tools and methodologies that enhance security without compromising efficiency.
Each key element, from intelligent security scanners to compliance automation, plays a pivotal role in fortifying the development pipeline against emerging threats while maintaining the agility for which DevOps is known. In the sections that follow, we explore these elements in detail, shedding light on how they contribute to a robust and resilient DevSecOps environment.
The purpose of DevSecOps in modern application delivery
The transition from DevOps to DevSecOps represents a significant paradigm shift in software development and deployment. While DevOps focuses on integrating development and operations to accelerate software delivery, DevSecOps takes it a step further by weaving security into the fabric of this integration. The objective is clear: to make security an intrinsic part of the development lifecycle rather than an afterthought.
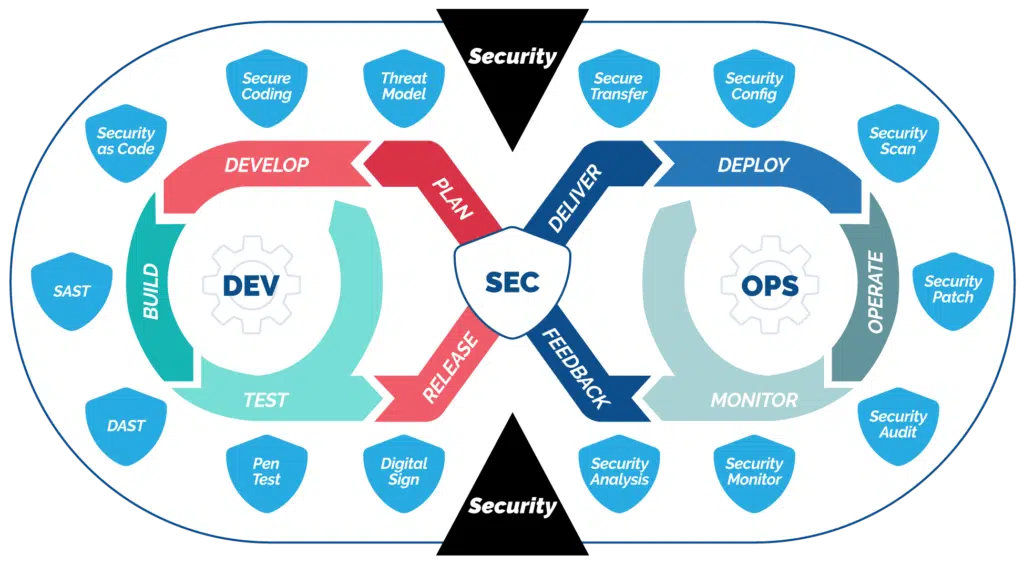
“Security as code” has been pivotal in this evolution. It advocates for the automation of security protocols, making them as fundamental as the code that builds the application. This approach allows security policies to be version-controlled and reviewed, just like any other codebase, ensuring that security is consistently applied across all development stages.
Automated security checks in CI/CD pipelines are another cornerstone of DevSecOps. These checks act as gatekeepers, scrutinizing code for vulnerabilities at multiple pipeline stages. By doing so, they reduce the risk of insecure code making its way into production while also speeding up the development cycle by eliminating manual security reviews.
“Suddenly, I can offer an engineer productivity! Where it used to take them roughly 40 hours to build up a system to overlay their tools, I deliver all of that in minutes with CloudBolt.”
Tooling and case studies
The real-world impact of DevSecOps is profound and far-reaching. In one instance, Etsy, an online marketplace, successfully implemented DevSecOps to achieve high deployment rates and build a strong DevOps culture. Its journey into DevSecOps has been well documented, showcasing how the company has reduced the number of security incidents while maintaining agility in deployments.
Similarly, Capital One, one of the largest banks in the US, has leveraged automated security checks in its DevOps pipeline to comply with stringent financial regulations. Its use of AWS has cut the time needed to build new application infrastructure by more than 99%, demonstrating the efficiency gains possible with a well-implemented DevSecOps strategy.
Modern multi-cloud management platforms like CloudBolt can elegantly complement this shift toward integrated security and efficiency. Regardless of how organizations address administering security—whether through DevOps teams implementing DevSecOps approaches or utilizing a PaaS offering—CloudBolt provides a centralized platform for managing security across hybrid cloud environments.
With standardized self-service resources via configurable blueprints, CloudBolt ensures consistent security levels for containerized applications, regardless of their origin. This centralized approach simplifies security management, enhances security posture, and reduces risk for enterprises adopting hybrid cloud frameworks.
In addition, CloudBolt offers the following built-in features to ensure continuous security and compliance:
- With CloudBolt, security shifts earlier in the software lifecycle. This approach involves codifying and controlling guardrails as code, subsequently reducing remediation costs by triggering compliance tests early.
- Continuously checks infrastructure setups and configurations to help enhance CI/CD processes. Key areas include data protection, pipeline health, network isolation, and integration with downstream tools.
- Supports over 150 integrations with leading tools like Palo Alto, Hashicorp, Splunk, and CyberArk to offer comprehensive risk protection.
Intelligent security scanners
The advent of AI and machine learning (ML) has significantly elevated the capabilities of security scanners. Intelligent security scanners that use AI/ML algorithms are now outperforming traditional vulnerability scanners, frequently with predefined rule sets as limitations. These advanced scanners can predict potential vulnerabilities by analyzing code behavior, offering a more proactive approach to security known as predictive security.
Predictive security is not just a buzzword: It’s a necessity in the current threat landscape. Intelligent security scanners can analyze vast datasets to identify patterns and anomalies that might indicate a security risk even before it becomes a threat. This predictive model allows organizations to take preemptive measures, reducing the risk of security breaches.
Tooling and case studies
Darktrace: This case study from the Darktrace blog discusses how cyber AI was used to defend against zero-day and N-day attacks that two different Darktrace customers faced. It describes the activity that Darktrace saw and what they did to stop it. The incidents are compared, and the risks of third-party integrations and the end of support for old security tools are discussed.
Ted Baker: In the Ted Baker case study, Darktrace’s self-learning AI was pivotal in mitigating cyber risks, addressing 4,000 threats weekly, including 200 targeted attacks. Darktrace Antigena, its autonomous response tool, was instrumental in swiftly responding to ransomware and protecting a broad range of digital systems, from email to point-of-sale devices. The AI system’s ability to learn normal user and device behavior enabled it to identify and neutralize threats without disrupting daily operations.
Ted Baker’s chief information officer emphasized the system’s rapid detection and response capabilities, allowing security teams to focus on higher-value tasks while the AI autonomously managed potential threats.
Paved roads in DevSecOps: charting a self-service route for secure development
The “paved roads” approach, which draws inspiration from Netflix’s strategy (described below), offers organizations a transformative path in DevSecOps. This methodology aligns with the principles of citizen development, where developers are provided with a guided “happy path” for self-service development. It integrates a structured yet flexible framework that includes preferred tools, practices, and processes, allowing developers to innovate within a secure and compliant environment.
This approach promotes efficiency and speed and embeds a deep sense of security within the development lifecycle. It’s about offering a well-maintained path—the “paved road”—that developers can follow to achieve swift, secure deployment without hindering their creative capabilities.
In practical terms, this means integrating automated security tools seamlessly into the CI/CD pipeline, enforcing code review protocols, and ensuring compliance with security policies. This strategy allows developers to push the limits while being very careful about security. It reflects the two main goals of DevSecOps: fast innovation and strong defenses.
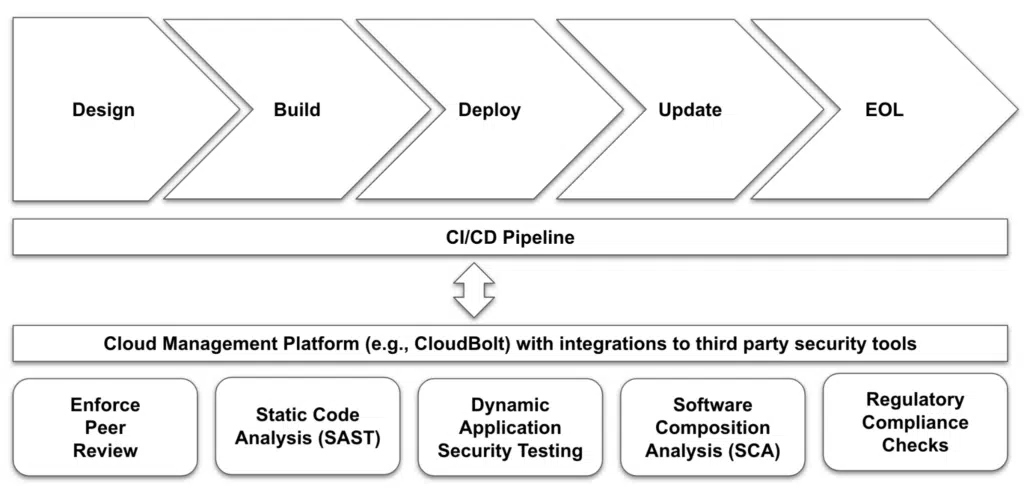
By mirroring Netflix’s model, organizations foster a culture where the boundaries of creativity and security merge, leading to the development of secure, high-quality software. It’s a pathway that accelerates the development process and fortifies applications against emerging cybersecurity threats. Paved roads in DevSecOps is about creating an environment where security is a springboard for innovation, not a constraint.
Tooling and case studies
Netflix’s DevSecOps implementation with the paved roads approach: Netflix has effectively implemented this approach in its DevSecOps practices, emphasizing seamless security integration throughout the software development lifecycle. A set of automated tools and methods, such as automated vulnerability scanning, code analysis, continuous monitoring, and log analysis, make this approach easier and are all built into their CI/CD pipelines.
Netflix’s embrace of the “security as code” paradigm is also crucial, using tools like Security Monkey for infrastructure as code (IaC), allowing consistent deployment of security infrastructure and policies. This comprehensive use of DevSecOps tools under the paved roads methodology ensures that security is integrated but also scalable and consistent across its vast infrastructure.
Segment’s paved roads strategy in DevSecOps: Segment, a customer data platform provider, adopts a DevSecOps approach that aligns with the paved roads philosophy. The security team at Segment emphasizes a consultative model, integrating early in the development process for threat modeling and design reviews.
A key aspect of the strategy is creating a paved road for developers where the adoption of security controls is user-friendly. This approach ensures that developers can easily follow secure practices without hindering their workflows. Segment’s strategy underlines the importance of empathy in security processes and a focus on creating secure environments that are both developer-friendly and robust in safeguarding against potential vulnerabilities.
“Developers are overwhelmed by the amount of security configurations that are needed to secure the cloud…they no longer have to be security experts or worry about creating vulnerabilities for the organization.”
CI/CD security gates
In continuous integration and continuous deployment (CI/CD), quality gates are checkpoints that validate the integrity of code before it progresses through the pipeline. When it comes to security, these gates are indispensable. They use dynamic security checks to stop a pipeline if holes are found, which is an essential way to protect against possible security breaches.
Tools like SonarQube play a pivotal role in setting up these security gates. They scan the code for vulnerabilities and code smells, providing real-time feedback that can be acted upon before the code is merged into the main branch.
However, the challenge lies in balancing speed and security. While it’s crucial to have these gates, they shouldn’t become bottlenecks that slow down the development process. The key is to implement asynchronous checks that run in parallel, allowing for both rapid deployment and robust security.
Tooling and case studies
Pipeline quality gate implementation: InfoQ discusses the importance of pipeline quality gates, providing insights into how software must meet enforced measures in the pipeline before proceeding. This real-world approach ensures that only secure, quality code is deployed.
Compromised CI/CD pipelines—real-world stories: NCC Group shares ten real-world stories of compromised CI/CD pipelines, highlighting the importance of security gates in preventing such breaches. This article provides valuable insights into the vulnerabilities of CI/CD pipelines and how security gates can mitigate these risks.
Threat monitoring and forensics
In a DevSecOps environment, real-time threat monitoring is not just a luxury: It’s a necessity. Detecting and responding to security incidents is crucial for minimizing damage and preventing future attacks. This is where tools like Splunk come into play, offering real-time data collection and analytics to identify abnormal patterns and potential security threats.
Post-incident analysis is equally important, and forensic tools can be invaluable. Tools like Wireshark can capture and analyze network traffic, providing insights into what went wrong and how to prevent similar incidents in the future.
Threat intelligence further enhances these capabilities by providing up-to-date information on emerging threats and vulnerabilities. These feeds can be integrated into monitoring tools to improve their detection algorithms.
Tooling and case studies
Dynatrace: In the federal and government sectors, Dynatrace has been used to assess an environment’s security posture, risk, and threat profile.
Cloud API logs: A case study on threat detection with Cloud API logs showcases how real-time monitoring can be effectively implemented (learn about the API security best practices).
Container lifecycle and application security: Red Hat’s integrated cybersecurity platform uncovers hidden threats and makes more informed risk-based decisions.
“We were surprised at how few vendors offer both comprehensive infrastructure cost management together with automation and even governance capabilities. I wanted a single solution. One vendor to work with.”
Resilience and chaos engineering
In DevSecOps, resilience is about not just bouncing back from failures but also proactively identifying weaknesses before they can be exploited. This is where chaos engineering comes into play. By deliberately injecting failures into a system, chaos engineering tests the system’s ability to withstand adverse conditions, thereby revealing vulnerabilities that might not surface under standard testing conditions.
Simulating security incidents is a crucial aspect of chaos engineering. By mimicking real-world attacks or system failures, you can assess how well your security controls hold up and where improvements are needed. Tools like Gremlin and Chaos Monkey are instrumental in implementing these simulated incidents, offering a range of “attacks” that can be unleashed on your system to test its robustness.
The insights gained from chaos experiments are invaluable. They provide a roadmap for strengthening your security posture, helping you understand what works, what doesn’t, and where you need to focus your efforts for improvement.
Tooling and case studies
Security flaw identification: Chaos engineering has been used to identify security flaws in DevSecOps pipelines, offering a proactive approach to vulnerability management.
Business continuity: Chaos engineering makes business continuity planning and disaster recovery real, thereby improving understanding of risks.
System architecture: By focusing on realistic use cases and system architecture, chaos engineering aligns with real-world scenarios, enhancing resilience.
Compliance automation
In a DevSecOps environment, the pace is fast, and the stakes are high. Manual compliance checks won’t cut it—they’re too slow and prone to human error. Automated compliance checks are the need of the hour, offering real-time audits and ensuring that the code meets all regulatory and organizational standards before it’s deployed.
Setting up automated compliance reporting is easier than you might think. DevSecOps engineers can perform these checks automatically by integrating tools like Chef InSpec and OpenSCAP into their CI/CD pipelines. These tools identify noncompliance and offer remediation advice, thereby streamlining the compliance process.
The “compliance as code” concept is gaining traction, allowing organizations to codify their compliance requirements and integrate them directly into their DevSecOps pipelines. This ensures a secure and compliant infrastructure that can adapt to changing regulatory landscapes.
Tooling and case studies
Copado: Automated compliance checks are driving enterprise adoption of DevSecOps, embedding test automation directly into version control.
OpsMx: Organizations are integrating and automating application security into CI/CD for continuous security and compliance.
McKinsey: Automated security test cases have streamlined controls by 50 to 80 percent without increasing risk.
Cloud cost management
Financial reporting in data centers has traditionally been fragmented, with rare instances of comprehensive FinOps reports covering both data centers and multiple cloud provider platforms. Research highlighted that 78% of enterprises had too many tools to help with automation silos, while 88% wanted an overarching solution that could not only emphasize collaboration among development, security, and operations teams but also promote a culture of cost-consciousness.
To support cloud cost management, various tools, such as Azure Cost Management (ACM) and AWS Cost Explorer, are tailored to specific platforms. These tools are excellent for organizations deeply integrated into their respective cloud ecosystems. Their platform-specific focus, however, limits them.
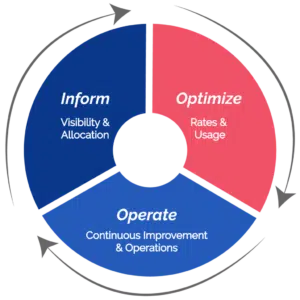
For companies that are either considering or have already invested in multi-cloud solutions, a platform-agnostic tool suite like CloudBolt emerges as an excellent choice.
Through its unified platform, CloudBolt addresses typical gaps by enabling organizations to attain financial clarity, eliminate wasteful spending, and deploy preventive controls for genuine FinOps success. The results are impressive, with CloudBolt customers reporting a significant reduction in manual financial processes and substantial savings within just 3-6 months of deployment.
Tooling and case studies
Optimizing cloud costs with CloudBolt: Companies have successfully implemented DevSecOps to optimize cloud costs using comprehensive management solutions.
AI-assisted orchestration: CloudBolt’s capabilities can be extended to orchestrate cloud computing costs effectively.
Cost management in pipeline security: CloudBolt ensures delivery quality, security, cost optimization, and compliance throughout the application lifecycle.
Conclusion
For businesses to remain competitive, the trick is to find the sweet spot between moving fast and staying secure. However, development teams are undergoing transformations in their workflows and adopting novel tools, so administering security isn’t a one-time task.
CloudBolt offers a comprehensive platform that aligns perfectly with these needs. CloudBolt’s foundation lies in hybrid cloud automation, providing an intuitive interface empowering even less technical practitioners to self-service application provisioning and maintenance.
CloudBolt encompasses true cloud management, cost control, and advanced FinOps. Learn how CloudBolt can help your organization transition from “cloud-first” to a “cloud-right” approach.
Related Blogs
The End of Manual Optimization: Why We Acquired StormForge
Today is a big day for CloudBolt—we’ve officially announced our acquisition of StormForge. This marks a major milestone for us…



